Contents
On September 1, a law office website in New Jersey suddenly went offline. Every administrator account was locked out at once — the first clear warning sign that the site had been hacked.
When I started digging, I found something even more disturbing. A WP core file (wp-config.php), the central configuration file for WordPress, was completely empty. With its database connection wiped out, the website simply couldn’t function. The hack was implemented via a file manager plugin that had a backdoor, in fact I found 3 file managers installed on the website!!!
Time was critical. For a law office, downtime isn’t just an inconvenience; it disrupts communications, client trust, and operations. Using a backup from August 31, I managed to restore the site the same day. But bringing it back online was only step one.
The First Signs of a Breach
Even after recovery, the initial security check turned up red flags:
-
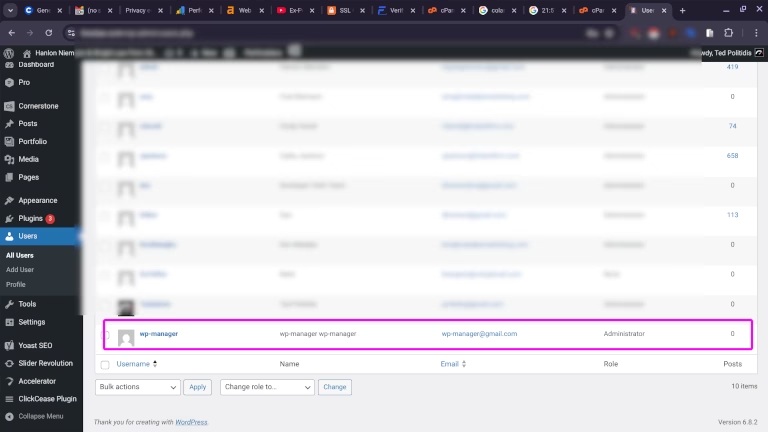
A strange administrator account named wp-manager, tied to a disposable email.
-
The primary security plugin had been disabled for an unknown amount of time.
This wasn’t a random glitch — it was clear the site had been compromised at a deeper level.
Deep Dive: Tracking the Malware
Once given a peek at the initial symptoms, the followup was to discover that the malware was masked as a wp plugin: theme_tools_wp.
This was far more than an ordinary headache. It ran silently alongside other processes while funneling complete control of the website to the malicious users. Here’s what it was doing:
— Spawning fake admin accounts like wp-manager and admlnlx.
— Hooking into legitimate administrator profiles, so passwords could be reset at will.
— Hiding its bogus accounts from the dashboard to stay out of sight.
— Blocking any attempt to delete or edit those accounts.
— Disappearing from the Plugins list, making itself practically invisible.
— Writing into the database to survive even if partially cleaned out.
— And when I tried to remove the infected files? They wouldn’t budge. That’s the classic hallmark of malware built for resilience.
The Cleanup
In order to recover from the attack, I:
— Removed the malicious theme_tools_wp plugin.
— Removed every single database reference related to the attack.
— Reset and secured every single admin account.
— Reenabled the security plugin and set it to a stronger mode.
— Added extra server-side protections to eliminate any backdoors.
Not only was the website cleaner at the end of the recovery but also more secure compared to before.
Lessons Learned
This incident underscores a few critical takeaways for law firms — and really, for any business running WordPress:
— Backups are non-negotiable. Without the August 31 backup, recovery would have taken far longer.
— Audit your users regularly. Suspicious admin accounts are usually the first sign of a breach.
— Keep security plugins active. A disabled firewall is an open invitation.
— Be cautious with plugins. File manager and unknown tools are often exploited as backdoors.
Even short lapses in security can open the door to attackers who don’t just break in, but stick around. Staying proactive is the only way to keep a site safe.

